“In days of old, Linus Torvalds didst create, A kernel for the masses, Twas Linux, oh so great! But little did we know, Twas child’s play all along, For Linus, the boy with blanket, also built his own. With wit and wisdom, both Linuses did combine,
To bring forth an OS, that’s truly one of a kind. But while one Linus doth wear a toga, The other, a blanket, like a security moga. But fear not, for building an OS is not so hard, For as Linus did it, so too can ye all, yard by yard.
And though some may scoff and say it can’t be done, Remember, in the world of potential probability, Everybody is Linus, everyone! So take up thy keyboard, and start to create, For in the end, the OS of your dreams, you shall sate. And when it’s done, and others do inquire, Just tell them, “Linus did it, hence, so can I, good sire.”
Different operating systems (OS) are optimized for specific usage scenarios. These usage scenarios can vary greatly, and the choice of OS can greatly impact the user experience.
- Windows – is a popular choice for desktops and laptops, it is also used in some servers. It is known for its wide range of software and compatibility with different hardware. It is used for general purpose computing and gaming.
- MacOS – is mainly used on Apple’s Macintosh computers and is known for its sleek design and user-friendly interface. It is popular among creative professionals for its design and multimedia software.
- Linux – is a versatile open-source operating system that is popular among developers, system administrators, and power users. It is known for its stability, security, and performance.
- iOS – is the operating system used on Apple’s iPhone and iPad devices. It is known for its ease of use and wide range of apps available through the App Store.
- Android – is the most widely used mobile operating system in the world. It is known for its customization options, and the wide range of apps available through the Google Play Store.
- ChromeOS – is a lightweight operating system designed for use on Chromebooks. It is known for its simplicity and ease of use, and its integration with Google’s web-based services.
- Ubuntu – is a popular version of Linux that is known for its user-friendly interface and wide range of software.
- Debian – is a version of Linux that is known for its stability and performance.
- Fedora – is a version of Linux that is known for its cutting-edge software and up-to-date packages.
- Kali – is a version of Linux that is popular among penetration testers and security researchers, it is known for its wide range of tools used for penetration testing and forensic analysis.
Each OS has its own set of strengths and weaknesses, and the choice of OS will depend on the specific usage scenario. For example, Windows is generally better suited for gaming, while MacOS is better suited for creative professionals. However, one can use virtual environments to simulate other operating systems, such as running Windows on a MacOS or a Linux machine, in order to use apps that are specific to that OS. This allows users to take advantage of the strengths of one OS while still being able to use apps that are only available on another OS.
![]()
Designing Your Operating System for Specialized Types of Usage Scenarios;
Here are three of the easier to modify open source operating systems, used by Developers for designing an operating system specialized for pentesters.
There are several open-source operating systems that are commonly used as a base for designing an operating system specialized for pentesters, but three of the most popular ones are:
- Kali Linux: Kali Linux is a Debian-based distribution that is specifically designed for penetration testing and security research. It comes with a wide range of pre-installed tools and utilities that are commonly used in penetration testing, such as Nmap, Metasploit, and Wireshark. It’s easy to customize and modify, making it a popular choice for pentesters.
- BlackArch Linux: BlackArch Linux is a lightweight and flexible penetration testing distribution based on Arch Linux. It comes with a wide range of tools for information gathering, vulnerability analysis, and exploitation, and it’s easy to customize and modify.
- Parrot OS: Parrot OS is a Debian-based distribution that is designed for penetration testing, forensic analysis, and privacy protection. It comes with a wide range of tools and utilities, including Metasploit, Nmap, and Wireshark. It’s easy to customize and modify, and it offers a user-friendly interface.

These operating systems are well-suited for pentesters because they come with a wide range of pre-installed tools and utilities that are commonly used in penetration testing, and they are easy to customize and modify to suit the specific needs of the pentester. Additionally, they all have active communities of developers and users that contribute to the development and maintenance of the operating systems.
Here are three of the easier to modify open source operating systems, used by Developers for designing an operating system specialized for Content Creation.
There are several open-source operating systems that are commonly used as a base for designing an operating system specialized for content creators, but three of the most popular ones are:
- Ubuntu: Ubuntu is a widely used open-source operating system that is based on the Debian distribution. It is known for its stability, performance, and ease of use. It is a popular choice for content creators because it comes with a wide range of software, including graphic design and video editing tools, as well as a wide range of multimedia software and codecs. It’s also easy to customize and modify, making it a great choice for content creators.
- Mint: Mint is a Linux distribution that is based on Ubuntu and Debian. It’s known for its user-friendly interface and its wide range of software. It comes with a wide range of multimedia software, graphic design, and video editing tools, making it a popular choice for content creators.
- elementary OS: elementary OS is an open-source operating system that is based on Ubuntu. It’s known for its sleek design and user-friendly interface. It comes with a wide range of software, including graphic design and video editing tools, as well as a wide range of multimedia software and codecs. It’s also easy to customize and modify, making it a great choice for content creators.
These operating systems are well-suited for content creators because they come with a wide range of pre-installed software and multimedia codecs, including graphic design and video editing tools, and they are easy to customize and modify to suit the specific needs of the content creator. Additionally, they all have active communities of developers and users that contribute to the development and maintenance of the operating systems.
UBUNTU (Kubuntu Theme GUI)
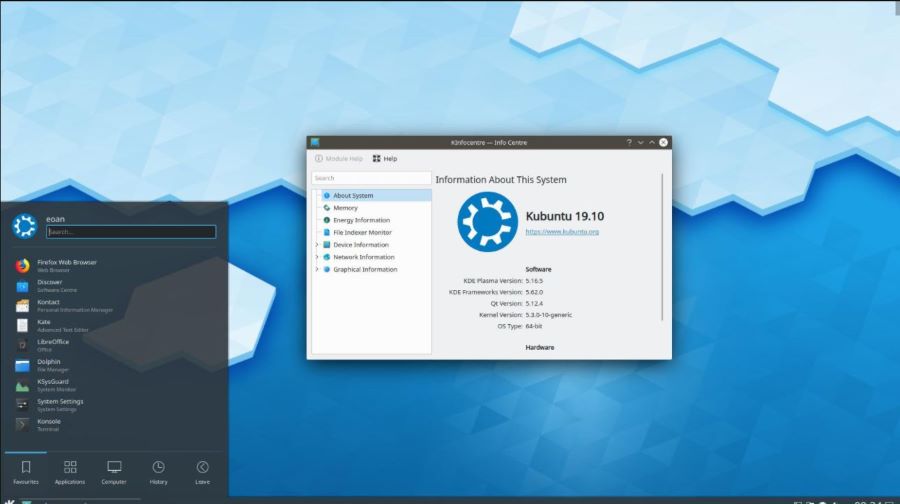
Here are what i consider to be three of the easiest to modify open source operating systems for designing an operating system specialized for Secure Browsing combined with Ample Compatibility for Content Consumption, Online Shopping, and Social Networking
There are several open-source operating systems that are commonly used as a base for designing an operating system specialized for secure browsing combined with ample compatibility for content consumption, online shopping and social networking, but three of the most popular ones are:
- Qubes OS: Qubes OS is a security-focused open-source operating system that is based on Xen hypervisor and Linux. It is known for its security features, such as compartmentalization, which allows different tasks to be isolated in different virtual machines. It has a built-in Tor support, and it allows easy integration of VPNs, making it a good choice for secure browsing.
- Tails: Tails is an open-source operating system that is designed for privacy and anonymity. It routes all internet traffic through the Tor network, making it a good choice for secure browsing. It also comes with a wide range of privacy-enhancing tools, and it’s easy to customize and modify.
- Whonix: Whonix is an open-source operating system that is based on Debian and built around the Tor anonymity network. It runs on a host operating system and uses virtualization to create a completely isolated environment for the Tor network, which provides a high level of anonymity. It’s easy to customize and modify and it’s compatible with most software used for content consumption, online shopping and social networking.
Cubes
These operating systems are well-suited for secure browsing combined with ample compatibility for content consumption, online shopping and social networking because they are designed to provide a high level of security and privacy while browsing the internet. They also come with a wide range of tools and features that allow easy customization and modification, making it easy to add compatibility with various software used for content consumption, online shopping and social networking. Additionally, they all have active communities of developers and users that contribute to the development and maintenance of the operating systems.
TAILS!
Tails, is an alternative operating system that is specifically designed for privacy and anonymity. It is based on the Linux distribution and is often referred to as an “amnesiac” operating system. Tails operates in a way that all the actions and data are stored in a RAM and once the computer is shut down all the data is lost, this helps to ensure that any sensitive information is not stored on the hard drive and can’t be accessed later.

Tails also incorporates a number of privacy-enhancing features such as the Tor network for anonymous internet browsing, and encryption for secure communication and storage. It also comes with a range of privacy-enhancing tools such as the Tor Browser, PGP encryption, and the ability to create and manage virtual private networks (VPNs).
Tails is primarily intended for individuals who are concerned about privacy and anonymity when using the internet, such as activists, journalists, and whistleblowers. It is also used by people who want to protect their identity and location while using the internet. Tails can be used on a USB drive or DVD and can be booted on any computer, regardless of the operating system installed on it.
In summary, Tails is a special kind of amnesiac operating system, designed for optimized privacy and anonymity whilst working, operating and browsing the internet. It’s a good alternative for those who want to protect their privacy and anonymity online, it’s also a good tool for those who want to keep their activities and data private, and doesn’t want to leave any trace behind.
Installation;
Installing Tails as a portable operating system on a USB drive or external hard drive is a relatively straightforward process. Here is a general overview of the steps:
- Download the Tails ISO file from the official Tails website.
- Insert the USB drive or external hard drive that you want to use as the Tails installation media.
- Use a software like balenaEtcher or Win32DiskImager to flash the Tails ISO file onto the USB drive or external hard drive. Make sure to select the correct drive before flashing the ISO file.
- After the flashing process is complete, safely remove the USB drive or external hard drive from your computer.
- Restart your computer and set the BIOS or UEFI to boot from USB drive or external hard drive.
- Tails will start up and you will be prompted to configure your keyboard and select a language.
- Once Tails is fully loaded, you will be presented with the Tails desktop. You can now use Tails as a portable operating system.
Alternatively, you can also install Tails on a drive partition of your existing PC, however, installing Tails on a partition of your existing drive, will leave some trace of your activity on your computer and it’s not recommended if you want to use Tails for anonymity and privacy.
It’s important to note that Tails is designed to be run as a live operating system, meaning that all changes made to the system are not saved permanently and will be lost once the computer is shut down. To save your work, you should use the built-in persistence feature to create a persistent storage partition on your USB drive or external hard drive. This will allow you to save your data and settings between sessions.
It’s also important to take regular backups of your persistent data to avoid data loss. Tails can be also configured to use a encrypted volume to store the persistent data, this will add an extra layer of security to your data.
USING WEB 3.0 Technologies and Apps, and A.I. assistants to empower and accelerate the project
OpenAI Codex and GPT-Chat can be used to speed up the task of creating one’s own operating system by generating code snippets that can be used in the system files of the operating system. The developer can use GPT-Chat and OpenAI Codex to generate code for various components of the operating system, such as the kernel, drivers, and system libraries.
For example, by providing GPT-Chat with a prompt describing the desired functionality of a new feature in the operating system, the model can generate code snippets that can be used to implement that feature. Similarly, OpenAI Codex can be used to generate code snippets for specific programming languages and libraries that are needed for the operating system.
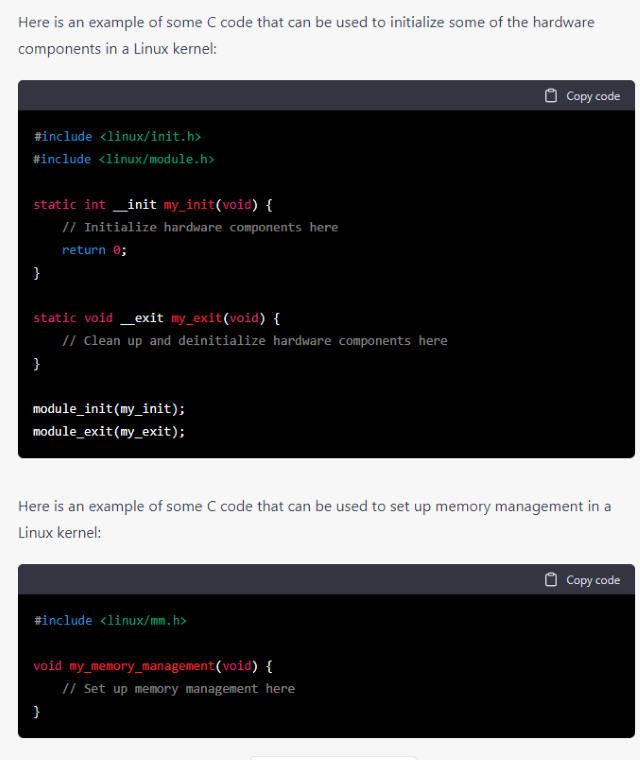
Additionally, GPT-Chat and OpenAI Codex can also be used to modify existing files within an open-source base operating system that the developer may take and use as the primary basis for the GUI. By providing GPT-Chat with a prompt describing the desired changes to the existing files, the model can generate code snippets that can be used to make those changes. This can save the developer a lot of time and effort compared to manually editing the code.
It’s worth noting that, while GPT-Chat and OpenAI Codex can be used to generate code snippets, it’s not a substitute for a human developer. The generated code may not be optimal, and it may require further testing, debugging, and validation, before it can be used in a production environment. Additionally, the developer should be familiar with the programming languages and libraries used in the operating system, in order to understand the code that GPT-Chat and OpenAI Codex generates.
In summary, GPT-Chat and OpenAI Codex can be used to speed up the task of creating one’s own operating system by generating code snippets that can be used in the system files of the operating system, and to modify existing files within the open-source base operating systems. However, it’s important to note that the generated code may not be optimal and requires further testing, debugging and validation before it can be used in a production environment.
Important Things to Consider when working with GPT Chat;
The imagination, and ability to phrase and paraphrase, when providing a prompt to GPT-Chat, are important factors in producing better results. By providing a clear and detailed prompt, GPT-Chat is able to understand the task at hand, and generate more accurate and relevant responses.
The accuracy of the prompt given, is also a major influential factor in the quality of output that GPT-Chat renders. If the prompt is not clear or is too broad, GPT-Chat may generate responses that are not relevant, or may not fully address the task at hand. Additionally, understanding how to speak to GPT-Chat in a way it understands is crucial to getting accurate results. It’s also important to note that GPT-Chat is trained on a large dataset of text, and its responses are based on patterns and associations it has learned from that data. Therefore, providing GPT-Chat with a diverse set of examples and prompts can also help to improve the quality of its output.
In summary, the imagination and ability to phrase and paraphrase when providing a prompt to GPT-Chat, the accuracy of the prompt given, and the ability of the prompter to understand how to speak to GPT-Chat in a way it understands, are important factors in the quality of output that GPT-Chat renders. The more accurate and detailed the prompt is, the better the output will be.
Here are three things I consider important to contemplate, before beginning to code and modify your operating system, and, understand the importance of outlining and designing the basic architecture of an operating system before beginning to code and/or modify, what one’s user interface should look and operate like, and what types of coding languages are most popular and apt for building an operating system from scratch, and which are most necessary to know, in order to modify an already existing open source operating system;
- Purpose and requirements: Before beginning to code and modify an operating system, it’s important to consider the purpose and requirements of the operating system. This includes determining the target audience, the tasks and functions the operating system will perform, and the hardware and software requirements. This will help to ensure that the operating system is tailored to the specific needs of the users and that it will be able to perform the intended tasks.
- Basic architecture: Before beginning to code and modify an operating system, it’s important to have a clear understanding of the basic architecture of the operating system. This includes understanding the different components of the operating system, such as the kernel, drivers, and system libraries, and how they interact with one another. This will help to ensure that the operating system is designed in a way that is efficient and scalable.
- User interface: Before beginning to code and modify an operating system, it’s important to consider the user interface. This includes determining the overall look and feel of the operating system, as well as the layout and functionality of the user interface. This will help to ensure that the operating system is easy to use and navigate for the users.
In terms of coding languages, C and C++ are the most popular and apt for building an operating system from scratch, as they are low-level languages that allow for direct manipulation of the hardware. However, modern operating systems also make use of other languages such as Python, Go, Rust and JavaScript.
Considering Modifying an Open Source Version of Linux is probably the best choice, one should consider the steps involved with building a Linux Kernel, and and create functions to include initializing the various hardware components, setting up memory management, and implementing system calls.
Creating a kernel using Linux is a complex task that requires a deep understanding of operating system concepts and a lot of low-level programming. The Linux kernel is a monolithic kernel and it’s source code is written in C and assembly, it’s not possible to write the kernel entirely in C++.
It would be logical to use C code language, to initialize the desired generic hardware components to be expected to be present within a Linux kernel:

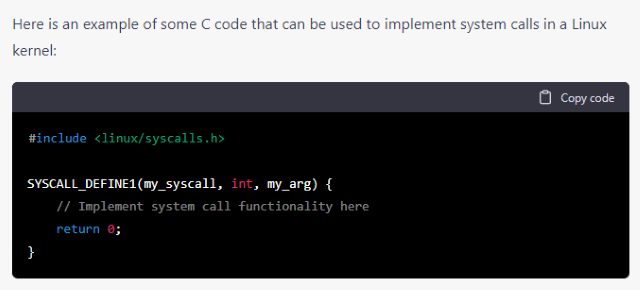
LEARN THE BASICS OF C CODE
Learning the Linux kernel source code can prove to be a challenging task, but it is also a rewarding one. Here is a step-by-step guide on how to start learning the Linux kernel source code:
- Familiarize yourself with the Linux kernel architecture: Before diving into the source code, it is important to understand the basic architecture of the Linux kernel. This includes understanding the different components of the kernel, such as the kernel, drivers, and system libraries, and how they interact with one another. You can find information about the Linux kernel architecture on the official Linux kernel documentation website.
- Get a copy of the Linux kernel source code: You can download the Linux kernel source code from the official Linux kernel website. It’s recommended to use the latest stable version.
- Learn the basics of the C programming language: The Linux kernel is written in C and assembly, so it’s important to have a good understanding of the C programming language. You can find many online resources and tutorials to help you learn C.
- Start reading the source code: Begin by reading the main() function in the kernel source code. This is the entry point of the kernel and it will give you an idea of how the kernel is initialized and started. As you read the source code, try to understand the flow of the code and the different functions that are being called.
- Learn about the Linux kernel subsystems: The Linux kernel is divided into different subsystems, each responsible for a specific task. Start with the subsystems that interest you the most and try to understand how they work and how they interact with other subsystems.
- Practice and experimentation: The best way to learn the Linux kernel source code is by experimenting with it. Try to modify the kernel and see how it affects the system. You can also try to write simple kernel modules to understand how kernel-space code works.
- Join a community: Linux kernel development is a collaborative effort, and there is a large community of developers who contribute to the project. Joining this community can be a great way to learn more about the Linux kernel and to get help when you need it.
- This is the first step in learning the Linux kernel source code, It’s a big task, and it requires a lot of time and effort, but with patience and persistence, you will be able to understand the Linux kernel and become a Linux kernel developer.
DOWNLOAD A PREVIEW OF MY SOON TO BE PUBLISHED E-BOOK “A complete guide to programming in C Language”